1. Click the Start Playcloud button. This will redirect you to the Queues section of the Amazon SQS.
2. On the list of SQS queues, select the SQS-Access-Policy
3. Click Access Policy.
Here, you can view the JSON policy document that specifies who can access the queue and what actions they can perform.
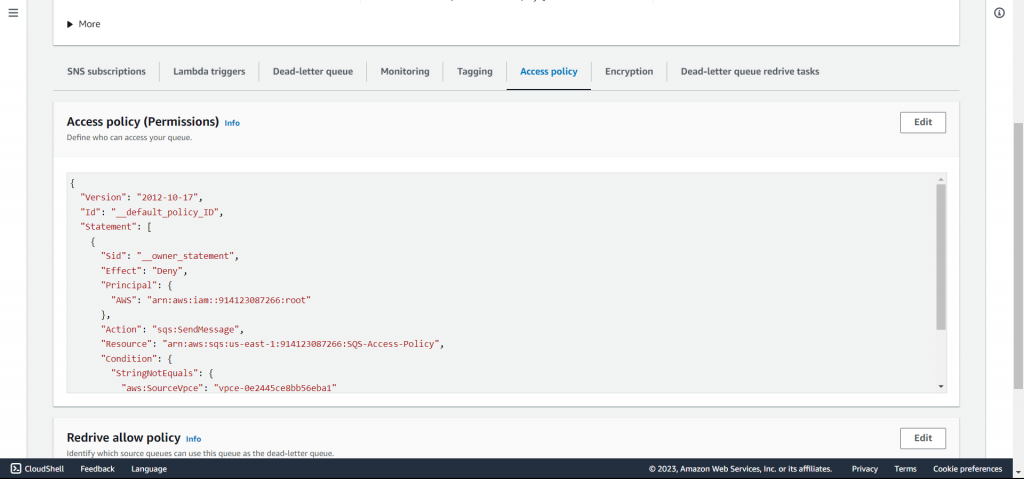
{
"Version": "2012-10-17",
"Id": "__default_policy_ID",
"Statement": [
{
"Sid": "__owner_statement",
"Effect": "Deny",
"Principal": {
"AWS": "arn:aws:iam::914123087266:root"
},
"Action": "sqs:SendMessage",
"Resource": "arn:aws:sqs:us-east-1:914123087266:SQS-Access-Policy",
"Condition": {
"StringNotEquals": {
"aws:SourceVpce": "vpce-0e2445ce8bb56eba1"
}
}
}
]
}This is an example of an AWS policy associated with an Amazon SQS Standard queue. Let’s break down the policy and understand each element:
- Version: The policy language version that is currently in use is indicated by this field.
- Id: This is an optional field that can be used to give a unique identifier to the policy.
- Statement: This field contains an array of one or more statements that define the permissions granted by the policy.
- Sid: This field is an optional identifier that can be used to provide a unique name to the statement.
- Effect: This field indicates whether the permissions in the statement are allowed or denied.
- Principal: This field specifies the entity or account that the policy applies to.
- Action: This field refers to the actions that are permitted or prohibited on a specific resource.
- Resource: This field specifies the Amazon Resource Name (ARN) of the resource to which the policy applies.
- Condition: This field offers further context or requirements that must be met before the permissions can be granted.
In this scenario, users can only send messages to the SQS-Access-Policy queue if their request is made from the designated VPC endpoint. This applies to all users and roles of the AWS account with the specified ID. If the request does not meet these criteria, access will be denied.
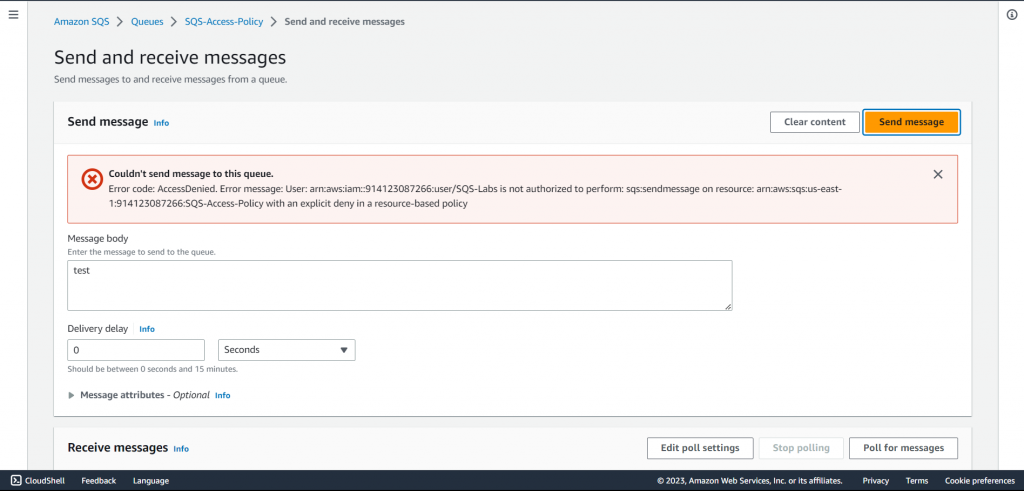
4. Try sending a message. You should receive an AccessDenied error due to the restrictions imposed by the access policy.